Signotaur Sign Action
The Signotaur Sign action allows you to sign files using the Signotaur service. This action provides various options to configure the signing process, including specifying the files to be signed, the signing server, and the signature details.
The Signotaur Sign action in Continua is a wrapper around the Signotaur client tool command line. If you're having trouble using the Signotaur Sign action, please refer to the Command Line Reference.
Signotaur Sign
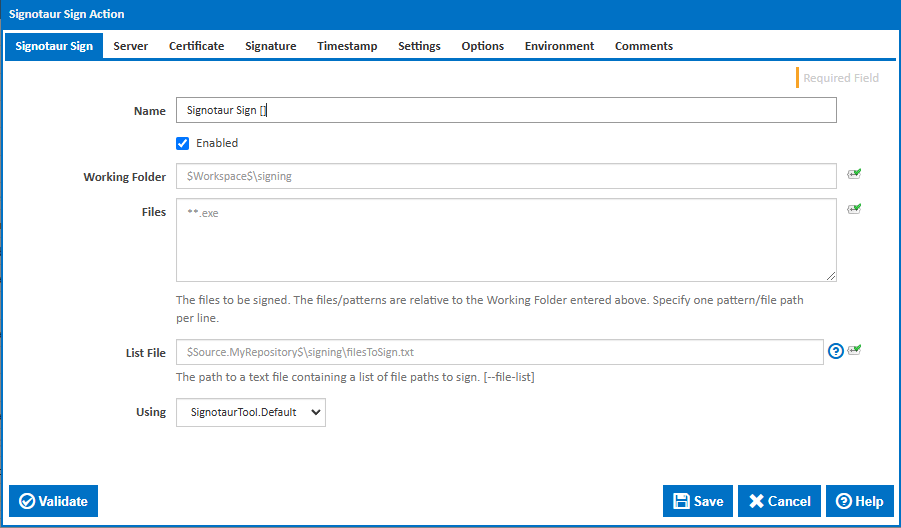
Name
A friendly name for this action (will be displayed in the actions workflow area).
Enabled
Determines if this action will be run within the relevant stage.
Working Folder
The folder where the files to be signed are located. This can be an absolute path or a path relative to the build workspace.
Files
Specify the file(s) to be signed. You can specify an exact file path or you can use ANT pattern matching to specify multiple files. Each file path or pattern must be entered on a new line. You can exclude files by prefixing the file name or pattern with a dash. e.g -*.ignore. Exclude patterns always take precedence over include patterns.
More information about pattern wild cards can be found on the Ant Pattern Usage page.
List File
The path to a text file containing a list of files to sign. This is helpful for signing multiple files at once without specifying each one in the command line. *[--file-list]
Using
The Using drop down is populated with any property collector whose namespace matches the pattern defined by the Signotaur action. The pattern for this action is ^SignotaurTool(?:\.|$). If you create a property collector for this action, make sure you select the Path Finder PlugIn type and give it a name that will match the pattern above. For more in-depth explanations on property collectors see Property Collectors.
Alternatively, you can select the Custom option from the Using drop down list and specify a path in the resulting input field that will be displayed. Please read Why it's a good idea to use a property collector before using this option.
Server
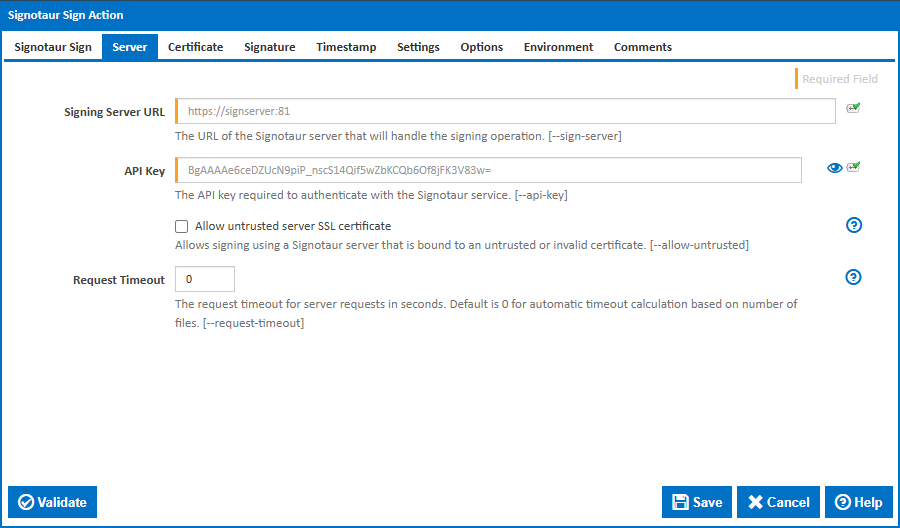
Signing Server URL
The URL of the Signotaur server that will handle the signing operation. This must be a valid HTTPS URL. [--sign-server]
Allow untrusted server SSL certificate
Allows signing using a Signotaur server that is bound to an untrusted or invalid certificate. Use this option with caution, as it may expose you to security risks. [--allow-untrusted]
Request Timeout
The request timeout for server requests in seconds. If the server takes longer than the specified time to respond, the operation will be aborted. Default is 0 for automatic timeout calculation based on the number of files. [--request-timeout]
API Key
Provide the API key for authentication.
API Key Source
Controls how the API key is provided to the action. The selected option determines which field is shown below.
Options:
- Value (default) – Enter the API key directly.
- File – Specify a path to a file containing the API key.
- Environment Variable – Read the API key from an environment variable.
Value
The value of the API key for authentication with the Signotaur server. [--api-key]
This field is visible when API Key Source is set to Value.
File
The path to a file containing the API key. The file should contain the API key as plain text or in dotenv format. [--api-key-file]
This field is visible when API Key Source is set to File.
Environment Variable Name
The name of the environment variable (or dotenv key) containing the API key. [--api-key-name]
This field is visible when API Key Source is set to File or Environment Variable.
Fail If Expiring Within
Fail the action if the API key expires within the specified duration. This allows you to proactively detect and rotate API keys before they expire. [--fail-if-expiring-within]
Certificate
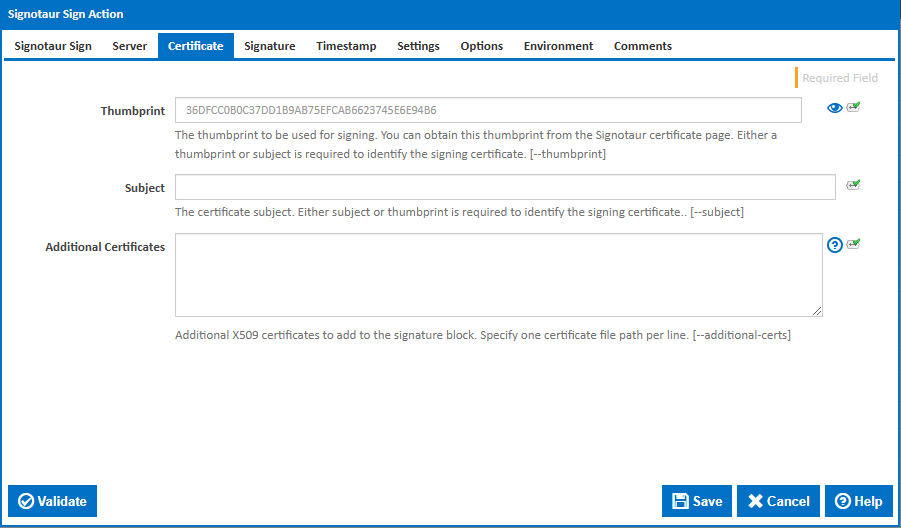
Selection Mode
Controls how the signing certificate is identified. The selected option determines which identification field is shown below.
Options:
- Thumbprint (default) – Identify the certificate by its thumbprint.
- Subject – Identify the certificate by its subject (Common Name).
- Label – Identify the certificate by a user-friendly label.
- Config File – Use a configuration file to specify the certificate.
Thumbprint
The thumbprint to be used for signing. You can obtain this thumbprint from the Signotaur certificate page. [--thumbprint]
This field is visible when Selection Mode is set to Thumbprint.
Subject
The certificate subject. [--subject]
This field is visible when Selection Mode is set to Subject.
Label
A user-friendly label assigned to a certificate on the Signotaur server. [--label]
This field is visible when Selection Mode is set to Label.
Additional Certificates
Additional X509 certificates to add to the signature block. Specify one certificate file path per line. This is useful for including intermediate or root certificates that may be necessary for validation. [--additional-certs]
Signature
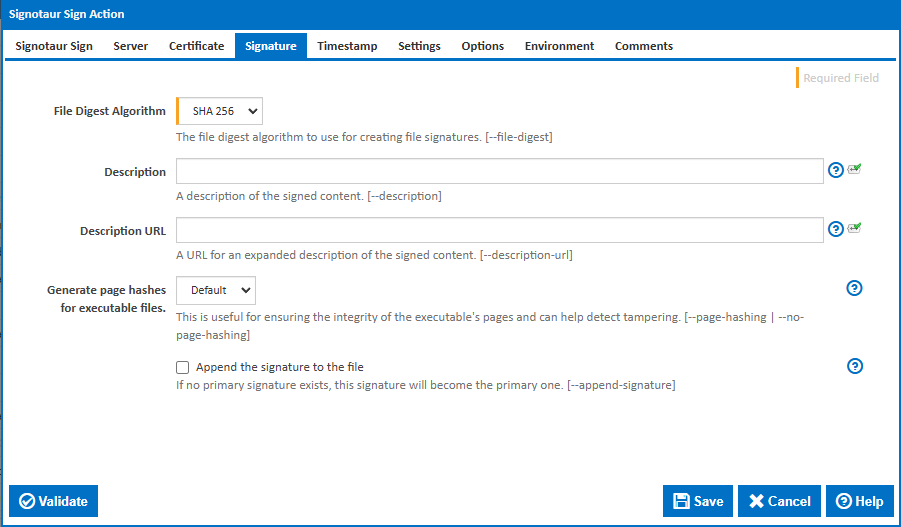
File Digest Algorithm
The file digest algorithm to use for creating file signatures. Options are: SHA 256, SHA 384 and SHA 512. The default is SHA 256. [--file-digest]
Description
A description of the signed content. This description will be embedded in the signature and should provide context about the content being signed. [--description]
Description URL
A URL for an expanded description of the signed content. This URL can point to a webpage or document that provides more detailed information about the signed files. [--description-url]
Generate page hashes for executable files
This is useful for ensuring the integrity of the executable's pages and can help detect tampering. Page hashing is only supported for executable files that have a valid PE header. This option will be ignored for files that do not meet this criteria.
The options are Yes, No or Default. If Default is specified, the system’s current configuration for page hashing will be used. If not explicitly configured, the default behaviour is to exclude page hashes. This setting is influenced by system-wide policies or defaults, such as those set by the WintrustSetDefaultIncludePEPageHashes function. [--page-hashing | --no-page-hashing]
Append the signature to the file
If no primary signature exists, this signature will become the primary one. This is useful for signing files multiple times without overwriting existing signatures. [--append-signature]
Add SHA-1 Signature
Create a dual SHA-1/SHA-256 signature for compatibility with older versions of Windows that do not support SHA-256 signatures. When enabled, an additional SHA-1 signature is appended alongside the primary signature. [--add-sha1-signature]
Deprecation Warning: SHA-1 is considered cryptographically weak. This option is provided only for legacy compatibility and should not be used unless you need to support Windows Vista or earlier. Microsoft has deprecated SHA-1 code signing.
Application Name
The name of the application or product (used only when signing ClickOnce and VSTO manifests). [--application-name]
Verification
Verify certificate chain before signing
When enabled, the action checks that each certificate in the chain is valid and issued by a trusted authority. This also enables the Revocation Check Mode and optionally Ignore untrusted root settings. [--verify-cert-chain]
Revocation Check Mode
Specifies how to check for certificate revocation when verifying the certificate chain. This ensures that no certificate in the chain has been revoked. [--revocation-mode]
Options:
- Online – Perform live checks against Certificate Revocation Lists (CRL) and OCSP servers (default).
- Offline – Use only cached CRL/OCSP information (faster if network access is restricted).
- NoCheck – Skip revocation checking entirely (higher risk).
This option is only available when Verify Certificate Chain is enabled.
Ignore untrusted root
Ignore errors caused by an untrusted or self-signed root certificate when verifying the certificate chain. Useful when signing with a private or internal CA. [--ignore-untrusted-root] This option is only available when Verify Certificate Chain is enabled.
Verify signature after signing
Verify the signature after signing to ensure it is valid. [--verify]
Strict Lifetime Enforcement
Enforce that the signature is only valid within the signing certificate's validity period. When enabled, signatures made outside the certificate's valid date range will fail verification. [--strict-lifetime]
This option is only available when Verify is enabled.
Timestamp
Timestamp Server URL
The URL of the RFC 3161 timestamp server. Time stamping is important for proving when a file was signed. If this option is not included, the signed file will not be timestamped, and a warning will be generated if timestamping fails. [--timestamp-server]
Timestamp Digest Algorithm
The digest algorithm used by the RFC 3161 timestamp server. This option is required if the Timestamp Server URL is provided. [--timestamp-digest]
Fallback Timestamp Server URL(s)
One or more URLs for RFC 3161-compliant timestamp servers to use as fallbacks if the primary timestamp server fails. Specify one server URL per line. [--fallback-timestamp-server]
Separate timestamping step
Run a separate timestamping step after signing. Automatically enabled when fallback timestamp servers are specified. [--separate-timestamp]
Settings
Skip previously signed files
Skip signing files that have already been signed. [--skip-signed]
Continue on failure
Continue signing subsequent files even if an error occurs while signing a file. This option is useful for batch signing scenarios where you want to attempt to sign all files regardless of individual failure. [--continue-on-fail]
Max Degree Of Parallelism
The maximum number of concurrent file signing operations. This setting allows you to control the degree of parallelism to optimize performance. The default value is 4, but you can adjust this based on the capabilities of your machine. [--max-degree-of-parallelism]
Automatically check for and install updates before signing
If an update is installed, the updated version is restarted with the same command line arguments, excluding this argument. [--auto-self-update]
Update Mode
Controls how the Automatically check for and install updates before signing feature determines when to update the Signotaur client. [--update-mode]
Options:
- SourceHash – Update only when the source code hash changes (default).
- Version – Update whenever a new version is available.
Visible only when Automatically check for and install updates before signing is enabled.
Options
Verbose logging
Log detailed output of the signing process. [--verbose]
No banner
Hide the banner for a clean log output. [--nb]
Timeout (in seconds)
How long to wait for the action to finish running before timing out. Leaving this blank (or zero) will default to 86400 seconds (24 hours).
Treat failure as warning
Tick to continue build on failure marking the action with a warning status.
Ignore warnings
If this is ticked, any warnings logged will not mark the action with a warning status.
Environment
Environment Variables
Multiple environment variables can be defined - one per line. These are set before the command line is run.
Log environment variables
If this is ticked, environment variable values are written to the build log.
Generate system environment variables
Tick this checkbox to set up a list of new environment variables prefixed with 'ContinuaCI.' for all current system expression objects and variables.
Mask sensitive variable values in system environment variables
This checkbox is visible only if the 'Generate system environment variables' checkbox is ticked.
If this is ticked, the values of any variables marked as sensitive will be masked with **** when setting system environment variables. Clear this to expose the values.