SecureZIP List Archive Contents Action
The SecureZIP List Archive Contents action allows you to display the contents of an archive.
List Archive Contents
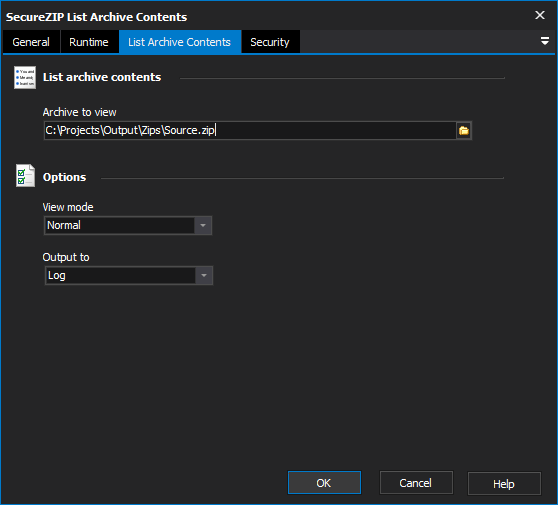
List Archive Contents
To view the contents of an archive, specify the archive in the field provided on the List Archive Contents page.
Archive To View
The zip archive to list all the files from.
Options
View Mode
The detail the generated file report should contain. There are three possible options;
Brief: A compact and less informative view of the file contents.
Normal: A relatively informative view of the file contents. Includes fields such as Size, Date, CRC, and Ratio.
Details: A very detailed view of all information held about files contained in the zip.
Output To
Whether to write the list of files to the log, a file, or both.
Output File
The file to write the list of files in the secure zip archive.
Security
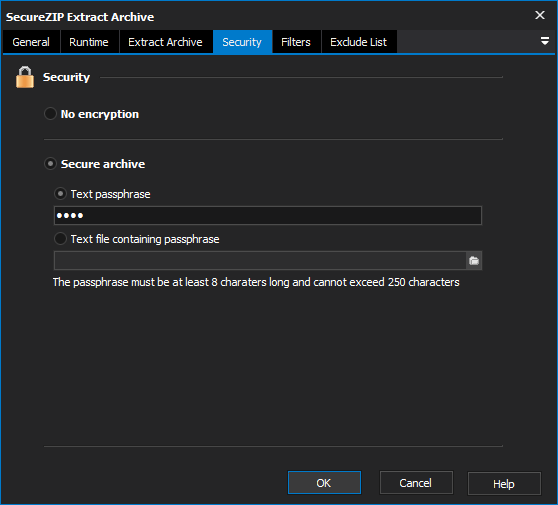
The Security Page allows you to work with secure archives.
Securing an Archive
When creating an archive the Security page offers two core options:
Security
To create a secure archive select the Secure Archive option and use the following security options provided:
The value for passphrase must be between at least 8 characters and not exceed 250 characters in length.
Accessing a Secure Archive
To access a secure archive you must provide the passphrase that was used to secure the archive.
On the Security Page specify the passphrase that was used to secure the archive. This can be done either of the two methods:
No Encryption
Set the archive to use no encryption as part of the archiving process when creating or updating the archive.
Secure Archive
Text Passphrase
A text phrase which is used by the encryption algorithm to encrypt the archive. Should be between 8 and 250 characters.
Text File Containing Passphrase.
A text file which contains a text phrase which is used by the encryption algorithm to encrypt the archive. Should be between 8 and 250 characters.
Use Strong Encryption
Whether to use a strong encryption algorithm. This will give greater security to the zip archive at the cost of time required for generating the archive and extracting from it.
Select Encryption Algorithm
The encryption algorithm to use during the strong encryption process. Each algorithms has its pro's and con's and we simply provide the ability to select the ones available on the tool. We suggest each should be reviewed for its potential weaknesses and what this means in your environment.
Encrypt File Names
Whether the names of the files include in the archive should be encrypted as well.